Understanding Oracles and Their Evolution
This module introduces the core problem that oracles solve: connecting isolated blockchains with real-world data. It explains the oracle problem, traces early centralized solutions, and shows how decentralized oracle networks emerged to reduce single points of failure. Learners will also discover the different types of oracles, the mechanics of data verification and delivery, and the transition toward programmable designs that add computation, randomness, and cross-chain communication.
Why blockchains need oracles
Smart contracts execute deterministically so that every node reaches the same result from the same inputs. This property secures consensus but isolates chains from the external world. Without a way to consume real-world information, smart contracts can only react to on-chain events. Markets, insurance, logistics, gaming, identity, and compliance all depend on data that originates off-chain. Oracles arose to bridge this gap by collecting external facts and furnishing them to contracts in a way that nodes can verify and agree upon.
The oracle problem
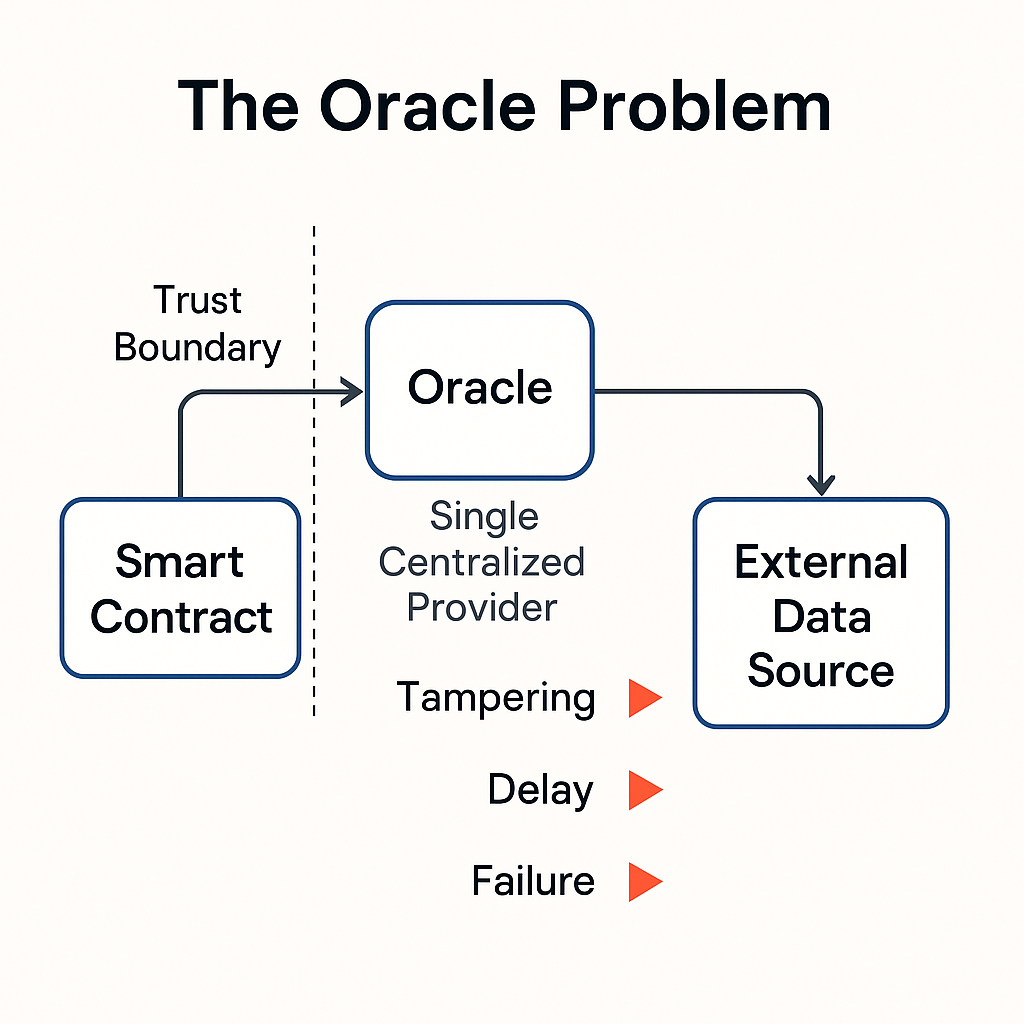
Introducing an external data source creates a new trust boundary. If a single party controls the data, the contract inherits that party’s reliability and incentives. A false or delayed input can cascade into liquidations, mispriced settlements, or halted protocols. The “oracle problem” is the challenge of delivering correct, timely data without recreating a centralized point of failure. The core questions are who provides the data, how multiple views are reconciled, and what evidence the chain receives to justify acceptance.
Early oracle designs
Initial approaches were simple relays that pushed API responses on demand. These designs made development easy but concentrated risk. They also struggled with latency during congested periods and lacked clear accountability when feeds diverged from reality. As decentralized finance grew, protocols required price inputs that were both tamper-resistant and available within block times. The response was to distribute oracle responsibilities across independent operators and to aggregate their reports on-chain.
Oracle types and data directions
Oracles differ by the direction and nature of the information they handle. Inbound oracles introduce external facts to contracts, such as market prices, weather readings, shipment scans, or identity attestations. Outbound oracles let contracts trigger actions in external systems, such as initiating a payout through a banking API or updating a logistics platform.
Software oracles source data from web services, while hardware oracles originate from devices like sensors and secure modules. Cross-chain oracles communicate state between ledgers so a contract on one chain can react to events on another. Each variant must address accuracy, timeliness, and resistance to manipulation within its context.
From single feeds to decentralized oracle networks
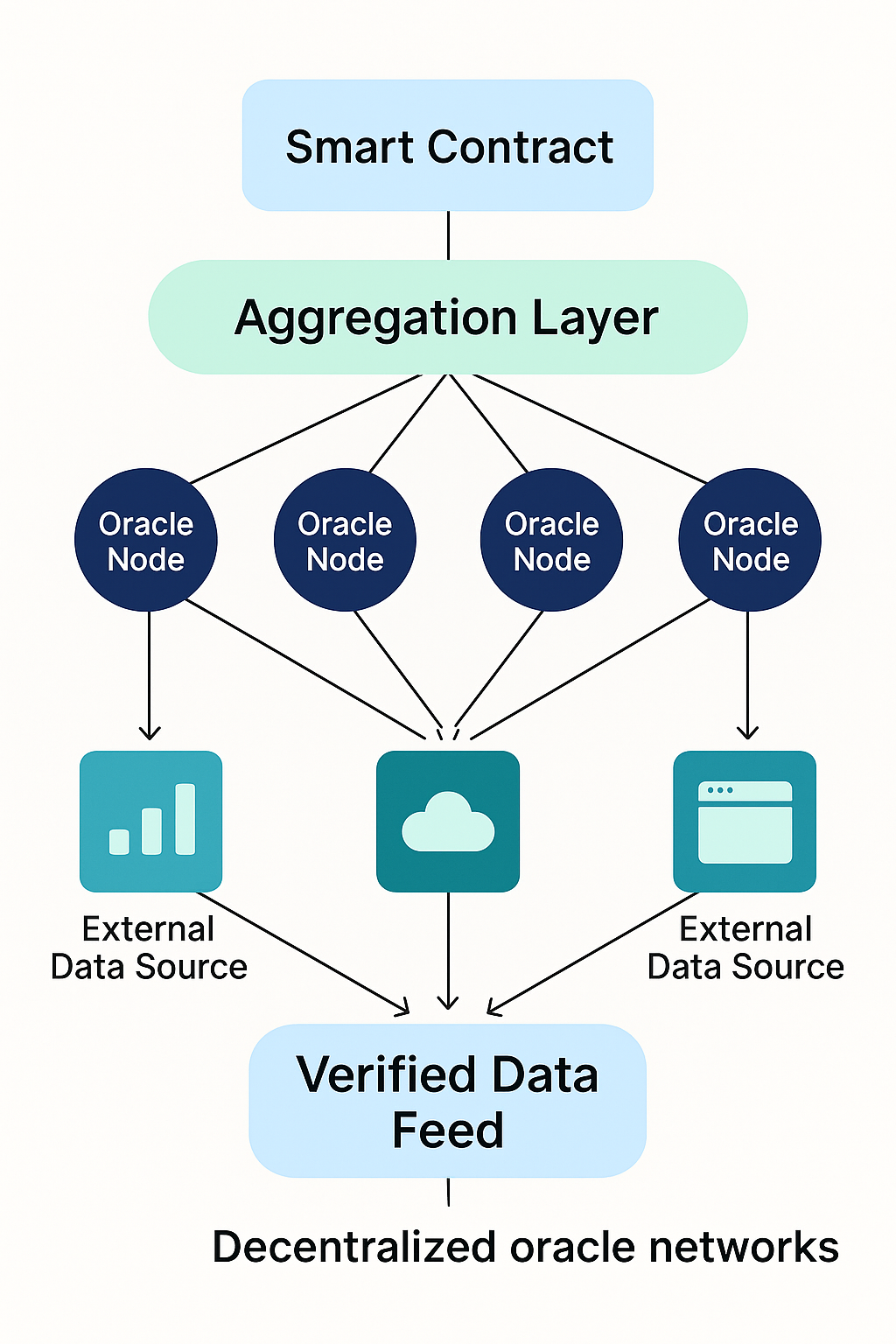
Decentralized oracle networks emerged to reduce the influence of any one provider. Multiple nodes fetch data from heterogeneous sources, sign their observations, and commit them to the chain. Contracts read an aggregate such as a median or weighted median. This architecture limits the impact of faulty or malicious reporters, provides redundancy against outages, and enables transparent auditing of feed updates over time. Network-level incentives and penalties further align behavior by rewarding honest reporting and discouraging deviation.
Data verification and delivery mechanics
A typical flow begins off-chain, where nodes query primary and secondary sources, normalize formats, and apply sanity checks. Observations are signed and transported to an on-chain aggregator contract that verifies signatures and computes the result. Update cadence balances freshness with gas costs. Some networks use push-based updates keyed to price deviation thresholds, while others allow pull-based reads that trigger an update on demand. Cryptographic techniques, such as threshold signatures or multi-party computation, can compress many attestations into a compact proof to reduce on-chain footprint.
The shift to programmable oracle networks
Static data relays limit expressiveness. Programmable oracle networks extend the model by allowing off-chain code to transform, validate, or compose data before delivery. Rather than providing raw weather readings, an oracle program can evaluate policy terms and compute a payout parameter. Instead of forwarding a single API value, it can reconcile multiple sources, filter outliers, apply domain-specific logic, and emit an auditable result. This approach moves certain computations to an environment that can access the full internet while preserving a verifiable link to the on-chain consumer.
Verifiable randomness as a specialized oracle service
Applications that depend on chance require unbiased, publicly verifiable randomness. On-chain pseudo-randomness derived from block variables is predictable to miners and validators. Verifiable random functions address this by having an oracle produce a random value and a proof that the value corresponds to a committed secret and request seed. Contracts verify the proof before using the value. This pattern underpins fair lotteries, game mechanics, randomized NFT traits, and any allocation that must resist manipulation.
Cross-chain messaging and state proofs
As ecosystems fragmented across multiple chains, oracles began to transport messages and state attestations between them. The simplest methods rely on federations that sign observations about events on a source chain. More advanced designs combine light-client proofs with committee attestations to prove inclusion of events without trusting a single party. The objective is to let a destination chain accept a message only when there is sufficient evidence that it was finalized on the source, thereby reducing the attack surface common in naïve bridge architectures.
Security models and failure modes
Oracle security rests on diversity of data sources, independence of node operators, robust aggregation, and transparent update policies. Attackers may target APIs, compromise operators, manipulate low-liquidity markets to sway reported prices, or exploit timing gaps between updates. Defenses include source whitelists with overlap, reputation and staking for operators, deviation-based circuit breakers, bounds checking, and fallback logic that freezes or slows updates when anomalies are detected. Formal verification of on-chain aggregation contracts and continuous monitoring of feed behavior further reduce operational risk.
Economic incentives and governance
Reliable oracles require sustainable economics. Networks compensate operators for fetching and reporting data, and may require collateral that can be slashed for provable misbehavior. Fee models must cover data acquisition, cryptographic overhead, and on-chain gas while remaining affordable for consumers. Governance determines how feeds are created, which sources are authorized, how operators are admitted or rotated, and how emergency procedures are invoked. Clear, precommitted policies reduce discretion during incidents and improve predictability for integrators.
Performance, latency, and cost trade-offs
Higher decentralization often implies more signatures to collect and more on-chain verification, which increases latency and cost. Conversely, smaller committees or single relays reduce expense but expand the trust assumptions. Update frequency also matters: frequent pushes improve freshness but raise gas usage, while sparse updates can be stale during volatility. Programmable designs add off-chain computation, which offers flexibility but introduces another surface that must be attested or audited. Each application selects a point along these trade-offs based on its risk tolerance and timeliness requirements.
Compliance, data rights, and provenance
Oracles interact with data that may be licensed, regulated, or privacy-sensitive. Providers must respect terms of use, maintain provenance records, and in some cases redact or aggregate personally identifiable information before publishing on public ledgers. For regulated venues, identity-gated feeds and permissioned delivery may be required. Provenance metadata and audit trails help downstream users assess whether a given value was produced under acceptable conditions.
Reliability engineering and operations
Practical deployments treat oracle networks as production systems with rigorous observability. Operators run redundant infrastructure across regions, monitor source health, and test failover paths. Canary feeds, shadow reporting, and simulated stress scenarios reveal weaknesses before they affect consumers. Incident response procedures define thresholds for pausing updates, rotating keys, or switching to fallback sources. Post-incident reviews feed back into configuration, source selection, and operator policies.
The trajectory of oracle evolution
Oracles began as ad hoc bridges that introduced significant trust. They evolved into decentralized networks that aggregate independent reports, then into programmable systems that execute domain logic off-chain while anchoring results on-chain. Specialized services such as verifiable randomness and cross-chain messaging extended their role from data provision to coordination across systems. The common thread is minimizing unilateral control while delivering the timeliness and expressiveness that real-world use cases demand. As programmable oracle networks mature, they function less like accessories and more like a parallel execution layer that complements on-chain contracts, allowing decentralized applications to interact safely and predictably with external data and computation.





